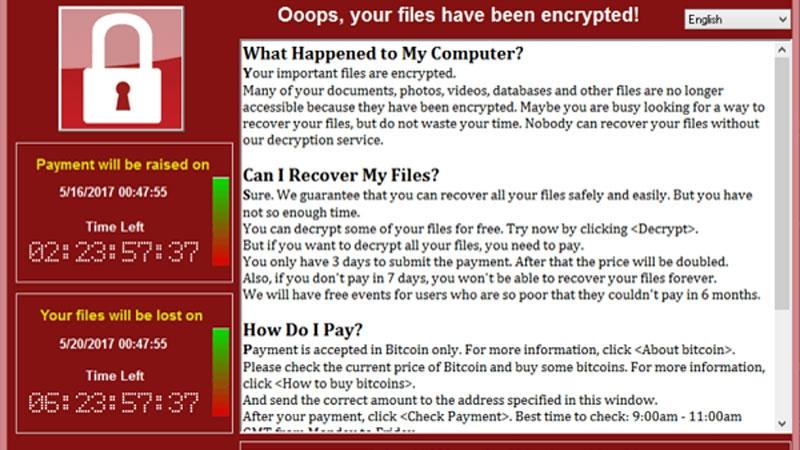
A French security researcher from Quarkslab, Adrien Guinet, discovered a way to retrieve the secret encryption keys used by WannyCry ransomware without having to pay.
The WannaCry encryption works by generating a pair of keys on the infected computer that rely on prime numbers. a public and private key for encrypting and decrypting the files on the infected machine.
Now here’s the fun part! WannaCry doesn’t erase the prime numbers used for the generation of the encryption keys before freeing the associated memory.
Based on this, Guinet releqse a WannaCry ransomware decryption, named WannaKey which basically tries to retrieve the two prime numbers used to generate the encryption keys from the memory.
The limitation of this method is though, that:
- The affected computer should not have been rebooted after being infected
- The associated memory should not have been allocated and erased by some other process.
The tool however, only pulls the prime numbers from the memory of the infected computer, so you can use those numbers to generate the decryption key manually to decrypt your WannaCry encrypted files.
Although, another security researcher named Benjamin Delpy, created a an easy to use tool called WanaKiwi, which is based on Guinet’s findings, to simplify the entire process of decrypting the WannaCry encrypted files.
The tool works on Windows XP, Windows Vista, Windows 7, Windows Server 2003 and 2008.
WannaKey:
https://github.com/aguinet/wannakey
WanaKiwi:
https://github.com/gentilkiwi/wanakiwi